
Cyber risk management portal
Being informed is the first step to being prepared.
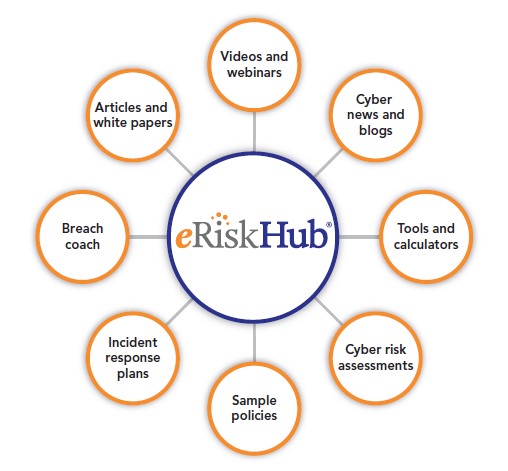
Hanover cyber policyholders receive complimentary access to numerous eRiskHub tools, including access to an online education portal powered by NetDiligence ®. The Hanover’s eRiskHub ® provides tools and resources to help you understand your exposures, establish a response plan, and minimize the effects of an attack.
Key features of The Hanover’s eRiskHub ® portal
- Incident roadmap — includes suggested steps to take following a network or data breach incident, free consultation with a Breach Coach® and access to a breach response team
- News center — cyber risk stories, security and compliance blogs, security news, risk management events and helpful industry links
- Learning center — best-practices articles, white-papers and webinars from leading technical and legal practitioners
- Risk manager tools — assists you in managing your cyber risk including a self-assessment and state breach notification laws
- eRisk resources — a directory to quickly find external resources with expertise in pre- and post-breach disciplines
The eRiskHub® portal is an effective way to combat cyber losses with minimal, controlled and predictable costs.
Get Started Today.
Current Hanover cyber policyholders can get started today by visiting https://www.eriskhub.com/hanover.php and completing the New User Registration form.
Note that you will need to locate the access code, which is included within the IMPORTANT POLICYHOLDER INFORMATION of your Hanover Cyber Advantage or Hanover Cyber Advantage Premier policy
*Upon initial log-in, there will be instructions to create a new password and login credentials.
Visit SiteBreach Protection Tips
| Use enterprise-grade Wi-Fi in your office
It must be secure, encrypted and behind a firewall. Access should require a unique username and password centrally controlled through the Wi-Fi hardware or an external directory authentication service. Integrating Wi-Fi with a directory service such as Microsoft Active Directory provides improved security. That’s because the credentials provided are the same as the standard network logon credentials. They must follow the same complexity and rotation rules. |
Install antivirus, anti-spyware and firewalls
Help prevent the mining of sensitive information by worms, Trojan horses, viruses and more, by installing the most recent enterprise-level antivirus, antispyware and anti-malware applications. Use firewalls to lock out hackers. |
| Regularly update all systems and software
Keep protection up-to-date by downloading recently issued system “patches” from antivirus and anti-malware registries, to defend against the latest forms of viruses, Trojan horses and other malicious software. |
| Evaluate contractor access to information
Evaluate whether contractors and vendors need access to any sensitive data. For example, employee personally identifiable information should only be accessed for payroll or benefit purposes. Your vendor agreements should provide adequate safeguards and ask vendors to: (a) abide by reasonable industry safeguards, (b) cover the costs and handling of any misuse or loss of sensitive data by their employees, and (c) have the financial capability to cover the costs to restore loss or damage, including remediation, by insurance coverage or bond. |
| Properly dispose of technology tools
Establish policies on how to destroy old computers, disks, tapes, CDs, memory devices and any other equipment that may contain sensitive information to prevent access by thieves. Don’t rely on the delete or trash functions to remove confidential files. To ensure complete destruction of the files, destroy the device. |

